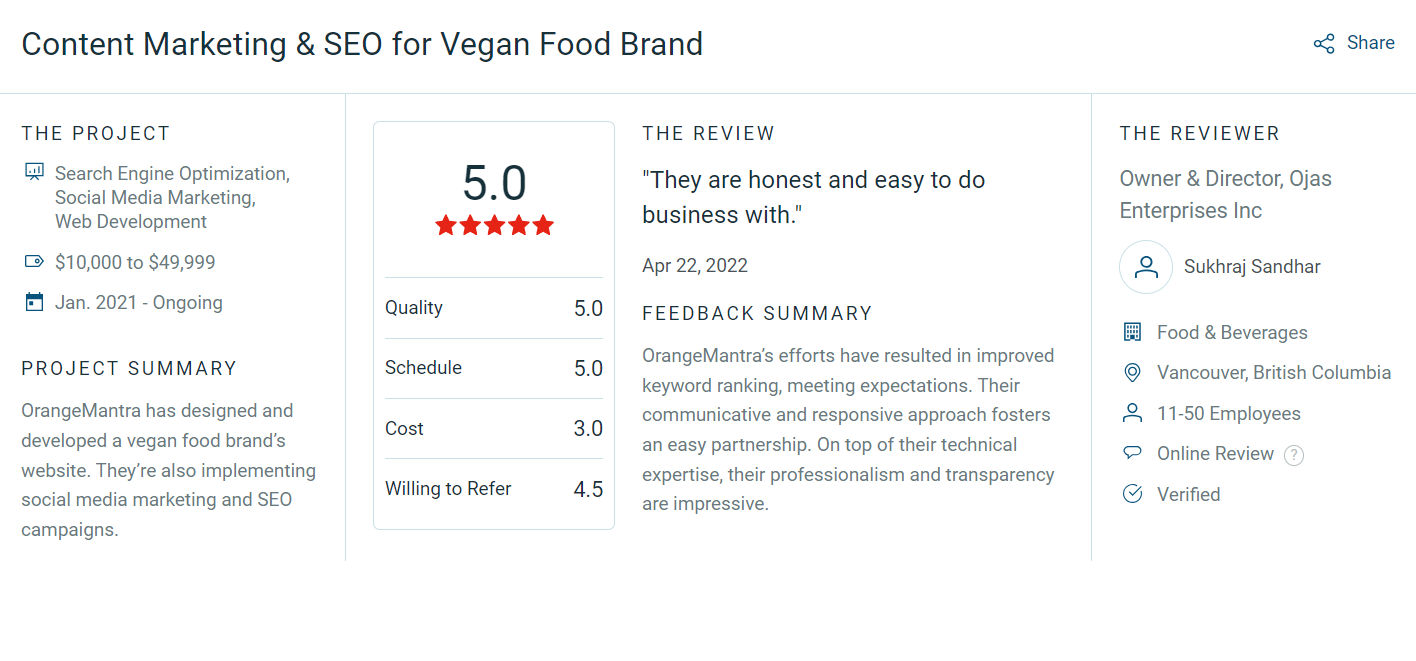
Managed Application Security Services
Protect your digital assets with our managed app security services as we take challenges out of your security posture. Our experts guide you in each stage.
Penetration Testing
Threat Detection and Monitoring
Mitigation Services
Customized Security Solutions






















 Java
Java  PHP
PHP  TypeScript
TypeScript  AngularJS
AngularJS  ReactJS
ReactJS  Vue.js
Vue.js  MySQL
MySQL  Redis
Redis  Cassandra
Cassandra  SQLite
SQLite