One wrong setting in the cloud can open the door to hackers.
This is the reality many companies face today.
More teams are using Microsoft Azure to run apps and store data. Azure is powerful and trusted. But using it safely is not automatic. You still need to protect your own data, users, and apps.
Azure has strong tools. But it works on a shared responsibility model. That means Microsoft protects the physical systems. While you are in charge of the rest—like who can log in, what data is stored, and how apps run.
In this blog post, we will discuss top Azure security best practices you need to follow in 2025. You’ll also get a clear Azure security checklist that your team can start using right away.
Why Azure Security Matters
Cloud environments are growing fast. But so are cyber threats. A small mistake in your Azure setup can cause big problems like data leaks or ransomware attacks.
According to recent studies:
- 80% of organizations faced at least one cloud security issue last year.
- Many of these issues happened due to weak identity access, open ports, or lack of monitoring.
This blog is your guide to avoiding such issues.
Understand the Shared Responsibility Model
Before we dive in, let’s quickly understand who handles what. Azure follows a shared responsibility model:
- Microsoft protects the hardware, network, and physical datacenters.
- You are responsible for things like your data, apps, users, and settings.
Depending on your service type:
- IaaS (Infrastructure as a Service) – You manage OS, apps, and data.
- PaaS (Platform as a Service) – You manage apps and data.
- SaaS (Software as a Service) – You manage access and user data.
This is why knowing your part is key.
Also Read: Revolutionizing Enterprises: The Latest Trends in Microsoft Azure for Digital Success
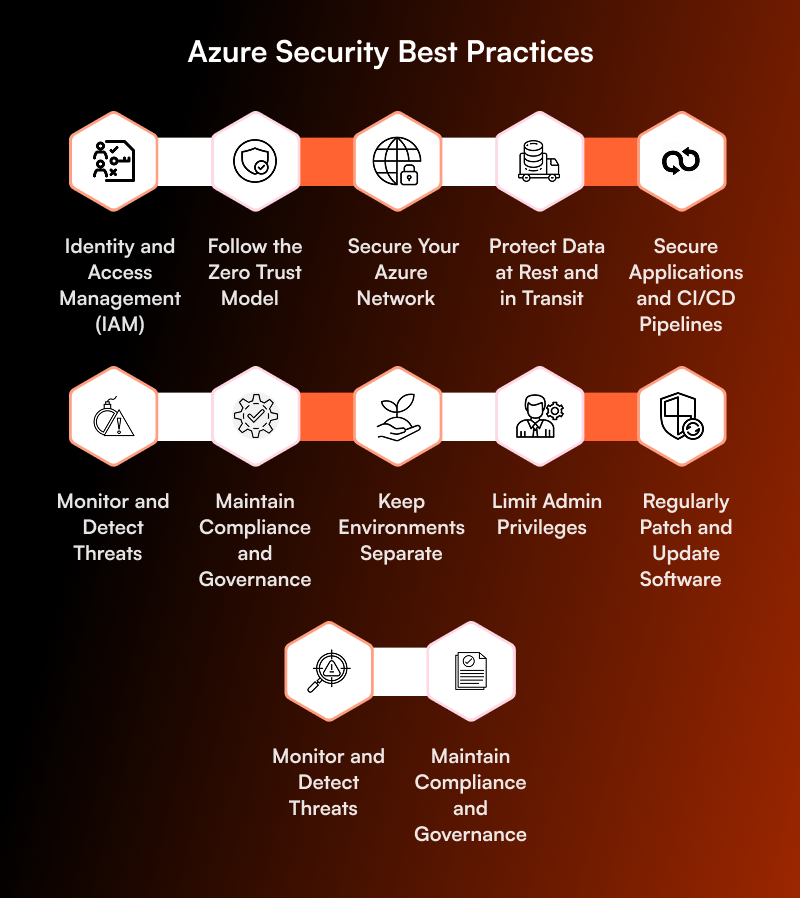
Azure Security Best Practices
Let’s have a look at Azure security best practices that one must keep in mind when planning a move to Azure. These are:
1. Identity and Access Management (IAM)
Start with identity. It’s the first door hackers try to open.
Use Azure Active Directory (AD)
Azure AD is the control room for your users and apps. Use it to manage logins, groups, and permissions.
Turn on Multi-Factor Authentication (MFA)
Passwords alone are not enough. Use MFA for all users, especially admins. MFA can block 99% of account attacks.
Use Role-Based Access Control (RBAC)
Give users the least access they need. Don’t make everyone an admin. With RBAC, you control who can do what.
Set Conditional Access
Create rules based on risk. Example: if someone logs in from another country, they require MFA.
2. Follow the Zero Trust Model
The world has changed. The next Azure security best practices include no longer trusting anything by default.
Never Trust, Always Verify
Check every access request. Don’t assume someone is safe just because they’re inside your network.
Use Just-In-Time (JIT) Access
Give access only when needed and for a short time.
Assume Breach
Design your system with the idea that someone might break in. Segment your network. Limit the damage.
3. Secure Your Azure Network
Your network connects all your services. It must be tight and controlled.
Use Azure Virtual Networks (VNets)
Create VNets to isolate resources. Use subnets for grouping and managing traffic.
Apply Network Security Groups (NSGs)
NSGs help control what traffic can come in and out. Always limit open ports.
Use Azure Firewall
Azure Firewall adds another strong wall around your network. It can block unwanted traffic and log everything.
Use Azure Bastion for VM Access
Don’t expose RDP or SSH to the internet. Use Bastion to connect to VMs securely.
4. Protect Data at Rest and in Transit
Data must be safe whether it’s stored or moving.
Encrypt Data at Rest
Azure encrypts your storage and disks by default. You can also use your own keys with Azure Key Vault.
Encrypt Data in Transit
Use TLS 1.2 or higher to protect data when moving between services.
Use Azure Key Vault
Store your keys, passwords, and secrets securely. Don’t hardcode them in apps.
5. Secure Applications and CI/CD Pipelines
Another Azure security best practices include having a secure from the inside out.
Enable Web Application Firewall (WAF)
Use WAF to block attacks like SQL injection and cross-site scripting.
Scan Code in CI/CD Pipelines
Use security tools in Azure DevOps to find bugs early.
Don’t Store Secrets in Code
Always store secrets in Key Vault. This keeps them out of Git or public places.
6. Monitor and Detect Threats
It’s not enough to set rules. You must watch everything.
Use Microsoft Defender for Cloud
This tool shows your overall security posture. It alerts you when something’s wrong.
Use Azure Sentinel
Sentinel is a powerful SIEM tool. It watches logs and detects threats across your system.
Set Alerts
Create alerts for failed logins, new admins, or open ports.
7. Maintain Compliance and Governance
Rules matter. You need to follow laws and company policies.
Use Azure Policy
Block risky actions, like deploying resources in the wrong region or leaving ports open.
Run Audits Regularly
Check who has access, what’s deployed, and what’s being used.
Use Compliance Manager
Track GDPR, HIPAA, and other laws. Get scores and fix what’s missing.
8. Keep Environments Separate
Don’t mix test and live systems. It can cause mistakes.
Use Different Azure Subscriptions
Have one for testing, one for development, and one for production. This keeps things clean and safe. If someone makes a mistake in testing, it won’t affect your real apps or users.
Apply Different Policies
You can set different rules and access levels in each subscription. This helps avoid confusion and stops accidents.
9. Limit Admin Privileges
Too many people with admin rights are risky.
Use Privileged Identity Management (PIM)
PIM lets you give admin access only when needed. For example, if someone needs to fix a server, give them access for just 1 hour. After that, their admin rights go away.
Ask for Approval
Make sure changes need a manager’s OK. This way, you know who is doing what.
10. Regularly Patch and Update Software
One of the Microsoft Azure security best practices is updating software for security patches at regular intervals. Old software is easy to attack.
Use Azure Update Management
It checks your virtual machines (VMs) and shows if anything needs updating. You can also schedule updates during off-hours to avoid downtime.
Don’t Delay Patches
Apply important updates as soon as they come out. Don’t wait.
11. Protect Your Databases
Databases hold your most important data.
Use Firewalls
Only allow access from certain IP addresses or apps.
Use Azure Private Link
With Private Link, your database is not exposed to the public internet. It only talks to services inside your network.
Monitor Access
Log who is accessing the database and when.
12. Apply Layered Security
Think of your system like a castle. Using many layers to protect it is one of the Azure security best practices.
Use Password + MFA
That’s two locks on the same door.
Use Conditional Access + RBAC
Set rules for who can access what, when, and how.
Use WAF + Azure Firewall
One protects the apps. The other protects the whole network.
Each layer makes it harder for hackers to get in. Even if one fails, others will still protect you.
BONUS: Don’t Forget These Small but Powerful Tips
- Clean up old user accounts
- Remove unused virtual machines or apps
- Tag all your resources for easy tracking
- Document your security settings
- Train your team on security basics
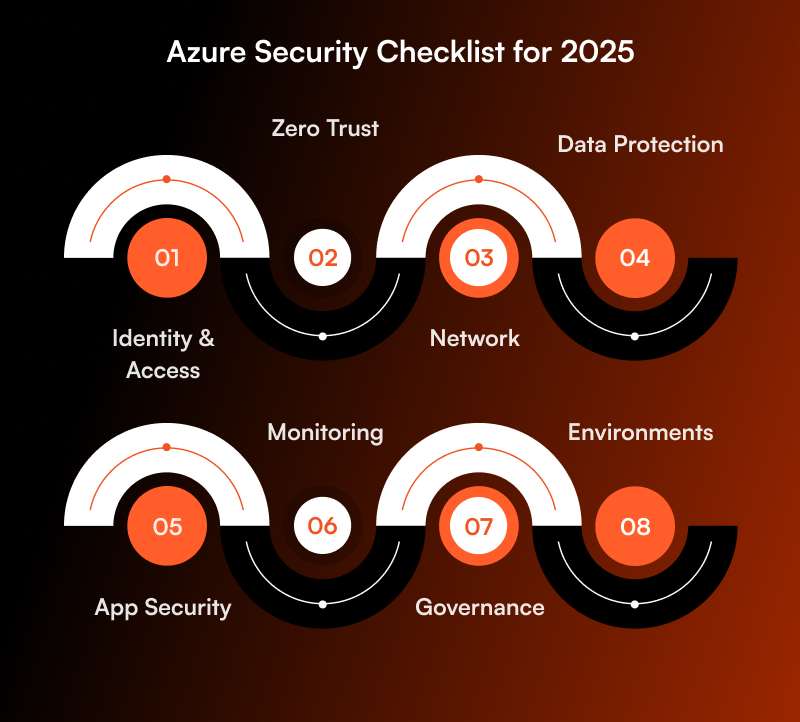
Azure Security Checklist for 2025
Here is your ready-to-use Azure security checklist:
Identity & Access
- Azure AD connected
- MFA on for all users
- RBAC in place
- Conditional Access rules active
- Access reviewed quarterly
Zero Trust
- JIT access enabled
- Network segmented
- Assume breach policies in place
- All traffic verified
Network
- NSGs applied to subnets
- Azure Firewall active
- No public RDP/SSH
- ExpressRoute or VPN used
- Bastion used for VM access
Data Protection
- Encryption at rest enabled
- TLS for all services
- Key Vault used for keys
- Backups tested
- Sensitive data labeled
App Security
- WAF in front of all apps
- Code scans in CI/CD
- No secrets in code
- Update Management configured
Monitoring
- Defender for Cloud enabled
- Sentinel active and tuned
- Alerts set for key events
- Incident response plan ready
Governance
- Azure Policies enforced
- Logs stored and reviewed
- Compliance Manager in use
- Unused resources cleaned
- Tags applied to all assets
Environments
- Separate subscriptions for dev, test, prod
- Policies applied to each
- Clear resource ownership
Final Thoughts
Following these Azure security best practices is not a one-time task. You must review and improve your setup regularly. Cyber threats are always changing, so your defenses must keep up.
Whether you’re setting up a new Azure environment or improving an old one, this guide can help. From identity protection to application security, every part matters.
If you’re planning to move your systems to the cloud or need help managing your existing environment, consider working with experts. Whether you’re looking to hire Azure developers or need Azure consulting services, make sure your partner is ready for today’s cloud risks.
OrangeMantra is a Microsoft Azure certified company that helps businesses across industries with cloud security, Azure migration services, compliance, and performance. We keep your systems safe while you focus on growth.