When it comes to protecting your business, understanding the nuances of both Cyber Security and Information Security is critical. To assist you in choosing the right strategy, we have written a comprehensive guide on the debate of Cyber Security vs. Information Security.
This post will provide the ultimate source of information to help you decide which solution is best for your business.
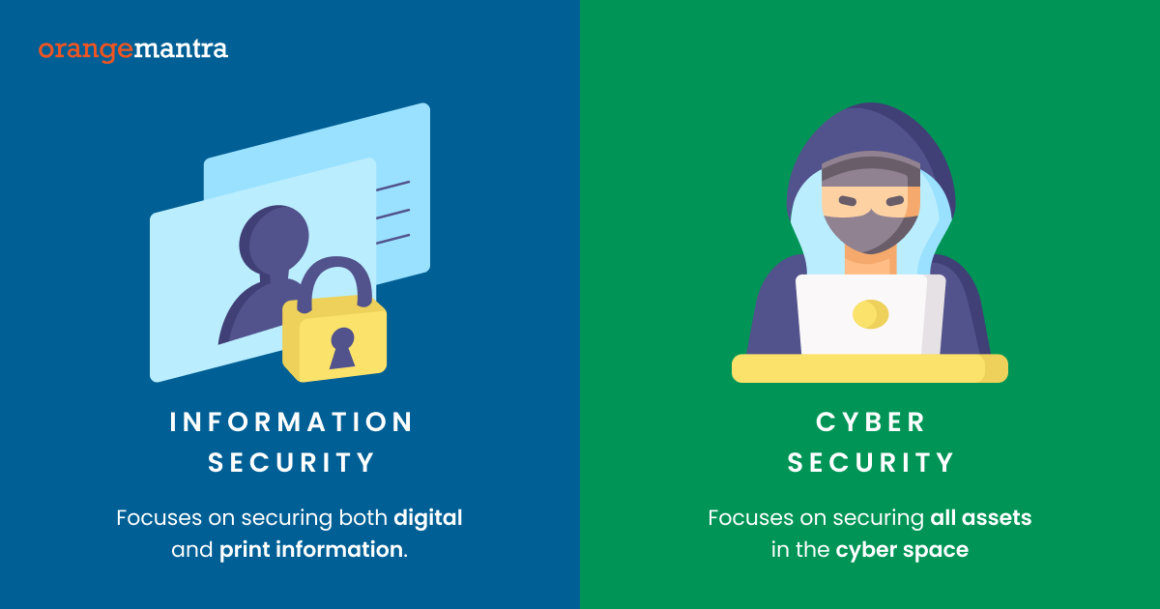
What is information security?
Safeguarding sensitive data from unauthorized access, modification, disclosure, use, and destruction is referred to as information security. Achieving this involves multiple technologies, policies, and practices which aim to preserve the integrity, confidentiality, and availability of information.
Security measures like encryption, firewalls, access management, and assessments help to secure data from malicious actors, while granting authorized personnel the information they require. Irrespective of the size and nature of an organization, the success of information security is pivotal.
Sure, here are the three basic components of information security:
- Confidentiality means that information is only accessible to those who are authorized to view it. This is often achieved through encryption and access controls.
- Integrity means that information is accurate and has not been tampered with. This is often achieved through data validation and checksums.
- Availability means that information is accessible when needed. This is often achieved through redundancy and disaster recovery planning.
Confidentiality
Confidentiality is the most important aspect of information security. If confidential information is leaked, it can have a devastating impact on an organization. For example, if a company’s customer data is leaked, it could lead to identity theft and financial losses.
There are a number of ways to protect confidentiality, including:
- Encryption – Encryption scrambles data so that it is unreadable without a key. This can be used to protect data at rest, such as data stored on a hard drive, or data in transit, such as data being sent over a network.
- Access controls – Access controls restrict who can access certain information. This can be done by using passwords, security tokens, or biometrics.
- Physical security – Physical security measures, such as locked doors and security cameras, can help to prevent unauthorized access to information systems.
Integrity
Integrity is just as important as confidentiality. If information is not accurate, it can lead to poor decision-making, financial losses, and even legal problems.
There are a number of ways to protect integrity, including:
- Data validation – Data validation checks incoming data to ensure that it is accurate and complete. This can be done by using checksums, which are mathematical algorithms that generate a unique value for a piece of data.
- Change management – Change management controls ensure that changes to information systems are properly authorized and tested. This helps to prevent unauthorized changes that could damage or corrupt data.
- Logging and auditing – Logging and auditing tracks changes to information systems. This can help to identify unauthorized changes and investigate security incidents.
Availability
Availability is the third pillar of information security. If information is not available when needed, it can lead to lost productivity, financial losses, and even legal problems.
There are a number of ways to protect availability, including:
- Redundancy – Redundancy creates multiple copies of information so that it is still available if one copy is lost or damaged. This can be done by using mirrored disks, load-balanced servers, or cloud-based storage.
- Disaster recovery planning – Disaster recovery planning outlines how an organization will recover from a major incident, such as a natural disaster or cyberattack. This plan should include steps to restore data, systems, and operations.
By understanding the three basic components of information security, organizations can develop a comprehensive security program that protects their data and assets. From just looking through it only won’t help. For more insights, we need to look into cyber security vs information security and understand the critical aspects related to it.
What is Cyber Security?
In order to guard against malicious cyberattacks like hacking, ransomware, and phishing. Also, it is necessary to implement defensive tactics like encryption, firewalls, data backup, and intrusion detection. These are major threats cyber security services cover.
Moreover, cyber security has become a vital necessity for individuals, companies, and organizations alike, not only for protection but for emergency responses and restoration plans in the event of a security violation.
1. Malware Attacks
Cyberattacks of a malicious nature, such as malware, are prevalent and damaging. This type of software is created to intrude on a computer or network, wreaking havoc in its wake and compromising the privacy of the user. It has the potential to cause data loss and inflict irreparable harm.
2. Phishing Scams
Hackers employ phishing scams as a major tactic for gaining access to sensitive information through emails, websites, or social media. Unfortunately, these scams often take advantage of people’s mistakes, leading to the theft of both personal and financial data.
3. Ransomware Attacks
In recent years, ransomware attacks have become rampant, locking up the files of its victims and asking for a monetary ransom to be paid in exchange for the decryption key. These malicious cyber-attacks can have detrimental effects on businesses, both in terms of operational interruption and financial damage.
4. DDoS Attacks
Through a DDoS (Distributed Denial of Service) attack, an influx of traffic from various sources floods a website or server, making it unresponsive or causing it to fail completely. Such incidents lead to drastic commercial losses, impairing customer service and causing lasting damage.
5. Insider Threats
Malicious activities carried out by people within a business, like personnel, contractors, or partners, are identified as insider threats. They may range from the theft of data to sabotage with the purpose of damaging security, or from unintentional blunders to negligent conduct. Either way, these may lead to severe violations of security.
6. IoT (Internet of Things) Vulnerabilities
With an ever-increasing population of connected devices, potential security vulnerabilities for IoT networks emerge. From the failure to create secure passwords to unsecured networks, any loophole can be exploited by malicious hackers to gain unauthorized access to valuable data or systems. To protect these devices, updates and patches must be routinely installed.
It is essential to identify and comprehend major cyber security threats to secure your organization from potential violations. Crafting a detailed security strategy can reduce any susceptibilities and ensure you stay prepared for the ever-changing risks.
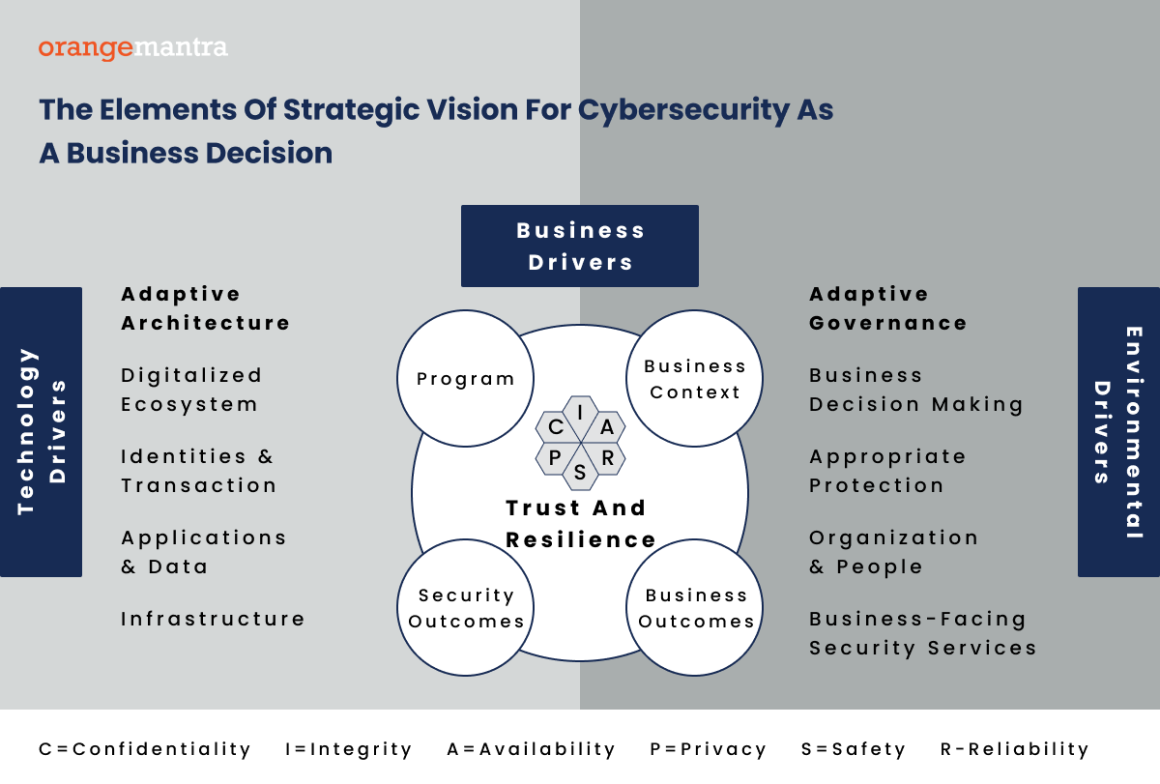
Cyber Security Vs Information Security: Major Different
Cyber security and information security are often used interchangeably, but they actually refer to two distinct areas of security. Understanding the difference between these two terms is crucial in selecting the right strategy to secure your organization.
Cyber Security
Cybersecurity is a discipline within the information security field. It covers the steps taken to protect internet-connected systems from malicious actors, including cyber-attacks, hacking, phishing, and malware.
The objective of cyber security is to prevent unauthorized access, theft, destruction, or interruption of hardware, software, and data. Cyber security specifically concerns threats related to digital systems and networks. To ensure their safety, it makes use of solutions such as antivirus software, intrusion detection systems, and security monitoring tools.
Unfortunately, cyber security also brings risks like phishing, malware, ransomware, denial-of-service attacks, and cyber espionage. As time goes by, these risks become more sophisticated due to the constant evolution of cyber criminals.
Information Security
Information security is a process that ensures data and information are not accessed, used, disclosed, altered, or destroyed without authorization. It involves the protection of intellectual property, financial information, digital and physical records, and personal information.
Moreover, regardless of how the data is stored, transmitted, or processed, it must be kept secure. This protection requires a comprehensive approach to maintain confidentiality, integrity, and availability of information.
Several methods, including encryption, access control, firewalls, and security policies, are used to protect information from any threats, such as data breaches, theft, sabotage, or insider threats. These threats can originate from physical, human, or technical sources.
| Feature | Information Security | Cyber Security |
|---|---|---|
| Scope | Protects all types of information | Protects information that is stored or transmitted over computer networks |
| Focus | Physical security, data security, and application security | Protecting information from attacks that occur over computer networks |
| Threats | Physical threats, data breaches, and application attacks | Cyber attacks, such as malware, phishing, and denial-of-service attacks |
| Tools | Firewalls, antivirus software, and intrusion detection systems | Security software, such as firewalls, antivirus software, and intrusion detection systems security awareness training for employees; and security policies and procedures |
Ultimately, cyber security falls under the larger umbrella of information security. Where information security takes a comprehensive approach to safeguarding data, cyber security emphasizes thwarting and responding to digital risks. It’s critical to pick the right solution based on your enterprise’s objectives, objectives, and dangers.
What to Know Which Strategy Is Right for Your Business?
Safeguarding digital possessions is an imperative factor in today’s interconnected environment. Thus, it is of utmost importance to pick an effective security tactic. Understanding cyber security vs information security is pivotal for any organization, yet how do you ascertain which one will be best suited for you?
Assess Your Needs
To select the best approach, you must begin by examining your needs. Are you responsible for securing confidential details, such as financial or personal data? Does your company operate within a regulatory-intensive sector, like healthcare or banking? Knowing your necessities can assist in determining the most effective strategy.
Consider Your Budget
When determining cyber security and information security, it is important to consider one’s financial resources. Firewalls and intrusion detection systems can be expensive investments when looking into cyber security, however, cheaper alternatives like encryption and access controls may be feasible when it comes to information security.
Evaluate Your Staff
Your team’s aptitude and technical ability are essential to contemplate when deciding between cyber and information security. Cyber security needs distinct expertise and understanding which may be beyond the capability of your personnel. Alternatively, access controls – part of information security – may be implemented more smoothly with a less tech-savvy team.
Evaluate Your Risk Tolerance
Risk-tolerance levels vary from business to business; some may feel more confident embracing a certain amount of danger, while others may not. Establishing an understanding of your own risk tolerance will allow you to decide which security system is the right choice for you.
Consider Your Industry
It is essential to assess the field you work in when deciding between cyber and information security. Businesses in the healthcare and financial sector have more stringent requirements and regulations, which make cyber security more suitable. On the other hand, enterprises which focus more on guarding intellectual property might favor information security.
Consult With an Expert
Uncertain of which approach is suitable for you? Then consulting with an experienced cybersecurity expert in cyber or information security could be a smart move. This way, you’ll be able to evaluate your situation and decide on the ideal strategy for your business.
Wrapping Up
Deciding the winner between cyber security vs. information security for an organization relies on the distinct needs of the organization. Being aware of the disparities and resemblances between these two techniques is essential to picking which one to focus on.
Both have their advantages and disadvantages, so it is important to assess them and establish which is most beneficial to the organization’s aims and targets. No matter which strategy is chosen, it is essential to remain proactive in locating and tackling any potential threats to ensure the organization’s information and possessions are protected.
By adopting the proper method and sources, it is possible to develop a secure basis that helps defend the business from any cyber-attacks. So, make sure to opt for cyber security services in India that present you with an incredibly talented skillset.
FAQs:
1- Who needs cyber security provisions?
Cybersecurity is essential in defending against unauthorized access or attacks against computers, networks, and the data and assets of individuals, businesses, and governments. Without proper security measures, all are at risk of being targeted by criminals.
2- What do security services providers do?
Cyber security service providers carry out a variety of tasks such as running assessments to discover potential threats, keeping watch over networks for unauthorized access, and handling security-related incidents. However, the range of services, as well as the approaches and pricing plans of providers, may differ significantly.
3- What are the services in cyber security?
To protect systems from security attacks, five distinct security services can be used: data confidentiality, data integrity, authentication, non-repudiation and access control. These services work together to ensure that all digital information is safe and secure.