We are living in a technology-driven world where we cannot imagine our existence without smart devices. We are used get real-time information and check crucial data from devices even when we are on the go. IoT is responsible for this. We are entirely dependent on this technology in many ways. The way we lead our lifestyle, and businesses irrespective of any sector, virtual devices, and in many other ways IoT is integrated, to make our lives easy.
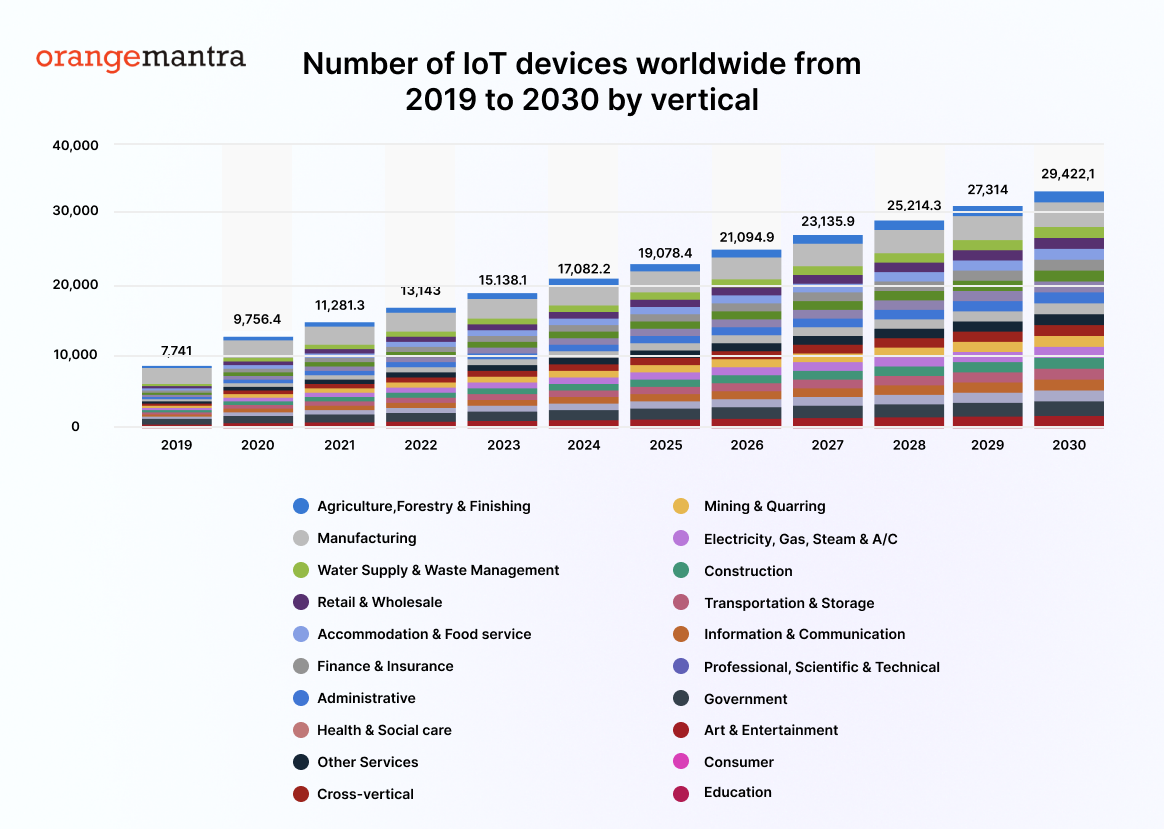
Almost approximately 15 billion devices are connected to IoT worldwide as per one of the latest reports by Statista reveal. This number is increasing continuously and is expected to double by the time of 2030.
Now let’s get started with the blog. In this piece of content, we will discuss some challenges that businesses face while incorporating IoT. Also, we will talk about the importance of cybersecurity in IoT.
Why Cybersecurity in IoT is Important for Your Business?
This is probably one of the most talked about cloud interfaces that users prefer to connect with their own smart devices. Most of the challenges with IoT interfaces are observed in industrial control systems and operational technology. These are more cyberattack-prone systems that act as threats to IoT-connected devices.
Cybersecurity experts have the expertise to understand core issues in the device that is connected to IoT. They highlight the problem of how cybercriminals become a threat to it and how they are capable of exploiting them. There are two major reasons why sometimes it becomes difficult to safeguard IoT-connected devices:
New brands keep on manufacturing new devices where they less concentrate on cybersecurity and that lead to more chances of getting affected by cybercrime.
The companies which have already incorporated cybersecurity are unaware of the multiple kinds of threats and more concerned about resolving cybersecurity issues that are associated with less budget. However, they must think of adjusting the budget as per the security concerns of the IoT devices.
Without cybersecurity in IoT, the chances of getting exposed to personal networks are high. Mostly industries like Finance, Defense, and healthcare have sensitive information to deal with. So, the incorporation of IoT demands extreme security to protect this information. If the IoT devices are not protected, the malicious attackers will destroy or tamper with all information in the network.
So in simple words, everything is linked to all other devices in the domain of IoT. So, in whatever business you are in, and whatever the size of your business is, you need to be always over cautious about the importance of cybersecurity in IoT.
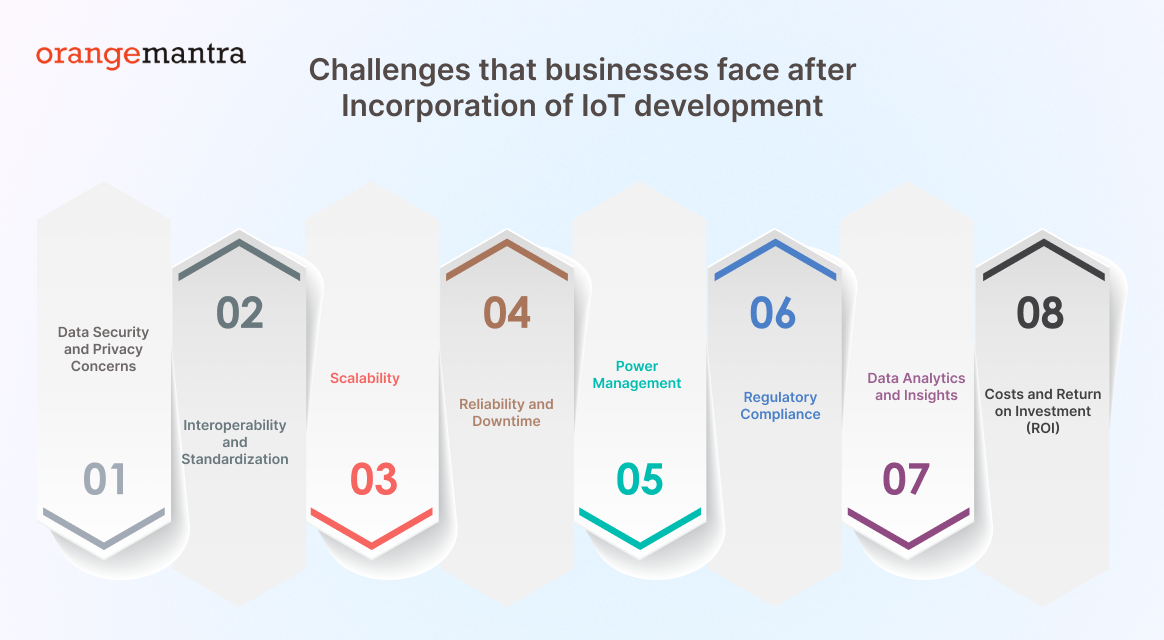
Top 8 Challenges that businesses face after Incorporation of IoT development
1. Data Security and Privacy Concerns
With the vast amount of data generated by IoT devices, ensuring the security and privacy of sensitive information becomes critical. Cyberattacks, data breaches, and unauthorized access are constant threats that businesses must address to maintain trust with their customers and partners.
2. Interoperability and Standardization
The IoT landscape involves a multitude of devices, protocols, and platforms from various vendors. The lack of standardization and interoperability can create compatibility issues, making it challenging for devices and systems to communicate effectively with each other.
3. Scalability
As IoT networks expand and the number of connected devices increases, businesses encounter scalability challenges. Managing a large-scale deployment of IoT devices, collecting and processing massive amounts of data, and maintaining network performance becomes complex tasks.
4. Reliability and Downtime
The reliability of IoT devices and networks is crucial, especially in critical applications like healthcare or industrial settings. Businesses face the challenge of minimizing downtime, as the failure of IoT devices or connectivity interruptions can lead to significant financial losses or even jeopardize human safety.
5. Power Management
Many IoT devices are constrained by limited power sources or rely on batteries. Businesses must optimize power management to extend the lifespan of these devices and reduce the need for frequent maintenance or replacements.
6. Regulatory Compliance
IoT devices often collect and transmit personal and sensitive data, subjecting businesses to various data protection regulations and compliance requirements. Adhering to these regulations and ensuring data is handled responsibly can be complex and resource-intensive.
7. Data Analytics and Insights
Gathering data from IoT devices is just the beginning. Extracting meaningful insights from the collected data is a significant challenge. Businesses need robust analytics solutions to process, analyze, and draw valuable conclusions from the vast volumes of data generated by IoT devices.
8. Costs and Return on Investment (ROI)
IoT development and implementation can be costly, especially when scaling up to support a large number of devices. Businesses face the challenge of balancing these expenses with the expected ROI, making sure that the benefits of IoT adoption outweigh the initial investment.
Addressing these challenges requires careful planning, ongoing innovation, and a proactive approach to mitigate risks and maximize the potential of IoT technologies in business operations.
How can you protect IoT-connected devices from Malicious Attacks?
IoT security concerns are not a new phenomenon. There are a lot of security measures that businesses could have taken but unfortunately, due to a lack of awareness of the variants, they failed to implement security protocols for IoT connectivity.
Now these vulnerabilities can cause due catastrophic consequences which are such as Brickerbot, Mirai botnet, Stuxnet, and Abbot. As these threats are concerning for internal business operations, therefore IoT vulnerabilities are taken seriously to withstand these issues.
They tend to opt for cybersecurity solutions for locking the holes, if there are any to protect against any kind of data breach. Therefore, to safeguard your IoT connections, you should be aware of the data breach or the gap and remove the cyber threats occurred in your business.
The following are some of the crucial IoT cybersecurity solutions that businesses can implement for safeguarding their IoT connections.
Read more: Cyber Security Vs Information Security: Everything You Must Know (2023)
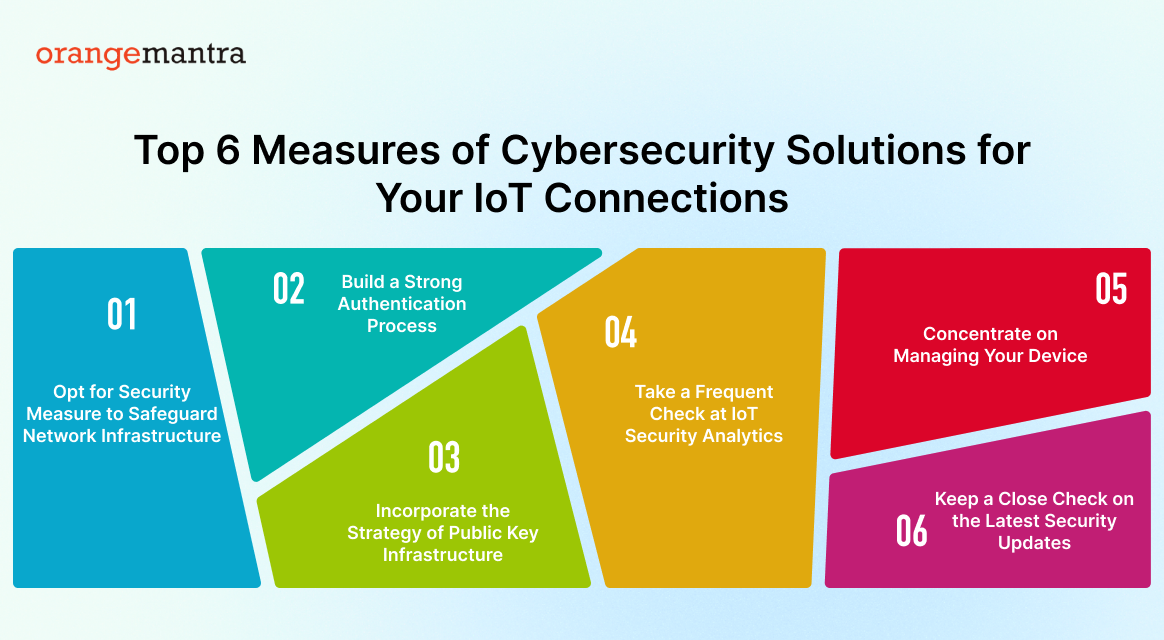
Top 6 Measures of Cybersecurity Solutions for Your IoT Connections
Cybersecurity in IoT is important for any business to protect its data interface. Now, the following measures will guide you to understand how can you secure the vulnerabilities for the ultimate growth of your business.
-
Opt for Security Measure to Safeguard Network Infrastructure
For every business where IoT is implemented, there is always a connecting bridge or better called a network between its backend system and the devices used in the operation. Now one needs to secure this network from getting affected by malicious cyber attackers. This is possible only when the need for safeguarding the connection is understood. This is only possible if you are implementing security measures such as firewalls, antivirus, VPNs, anti-malware, and different other preventive steps.
Once these measures are implemented, it will deny all unauthorized access. This will lead to preventing all malicious attacks that can be a threat to the business operation. Through this, you can secure your network infrastructure and ensure swift business activity.
-
Build a Strong Authentication Process
As cybersecurity and IoT are the two sides of the same coin, you need to be careful about choosing the right IoT cybersecurity solutions for your business. Among many other security measures, a strong cybersecurity measure is the authentication features for IoT-connected devices. The multi-authentication leverages you with double security measures in the process.
The biometric feature system and multi-factor authentication features don’t allow users who fail to authenticate their identity in the system. The features allow you to negate the entry and without your permission, nobody will be able to get the entry to the system.
So, if the suggested authentication feature is implemented, you will be able to safeguard your IoT devices. Thus, in this way you will enjoy the vast measures of cybersecurity in IoT no matter from anywhere the devices are operated.
-
Incorporate the Strategy of Public Key Infrastructure
This is one of the most crucial strategies to engage all users to start with a secured communication process in terms of money and information exchange. The Public Key Infrastructure strategy secures the communication channel and ensures data encryption.
The strategy works in two ways that are symmetric and asymmetric encryption processes. There are primary factors to these encryption processes. When some activity is done through encryption with the help of a public key, in this case, decryption is implemented through the private key.
This situation can be vice-versa in the case of the implication of the Public Key Infrastructure strategy. So this way IoT data cybersecurity is maintained, and there will less chances to face the threats of malicious actions.
-
Take a Frequent Check at IoT Security Analytics
There is one more parameter to understand and safeguard IoT-connected devices. By measuring and keeping a close check on the security analytics you can remove the threats on your IoT-connected devices.
The positive part of this feature is the collection of data, the analysis of it, and correlating parts involved in this. Multiple sources of data are analyzed after the required considerations, the IoT security providers assist you in identifying various potential threats.
Once the threat is detected you can immediately proceed to resolve them through the implementation of various cybersecurity tools in the business process.
-
Concentrate on Managing Your Device
The best approach for cybersecurity in IoT is the practice of managing threats in your device. A strong password settings strategy allows you to operate and monitor your device remotely.
The centralized control feature further allows you to identify the threats and then opt for required security measures. It is always important to choose unique passwords. Also, you need to change the passwords at certain intervals.
In this case, while we mention unique passwords, we mean passcodes that are easily guessable. This will restrict attackers to predict passcode combinations easily and will save you from getting malware threats.
-
Keep a Close Check on the Latest Security Updates
The matter of cybersecurity in IoT is not a new phenomenon. And companies are becoming aware of the malicious cyber threat reduction strategies, and implementing those cybersecurity solutions in their internal process. So, regarding this, there are several updates are released regularly. You need to keep a close check on these cybersecurity tools and incorporate them into your business.
Reconsider your IoT cybersecurity solutions with OrangeMantra
If you are already juggling with what cybersecurity solutions you should incorporate into your business operation, we at OrangeMantra assist you in identifying and providing the required solutions to it. We’ll be considering various cybersecurity solutions in our next piece of blog.
Concluding Thoughts
So, the above-mentioned vulnerabilities and challenges and procedures to safeguard will guide you to understand the type of threats. The incorporation of Cybersecurity in IoT will allow you to protect your sensitive data and lead you to reach your business goal.
FAQs
1. Is IoT an inseparable part of IoT?
IoT security solutions are the necessary measures that businesses are incorporating in their internal process to remove the chances of cyber threats to the system.
2. How can cybersecurity solutions IoT develop?
There are various cybersecurity solution measures available that are addressing the cyber attacks and helping businesses to secure their process.
3. What are the examples of cyber security in IoT?
Examples are WiFi-capable automobiles, networked security cameras, and smart refrigerators.